M365 Relay Attack: A Live Example (August 2024)
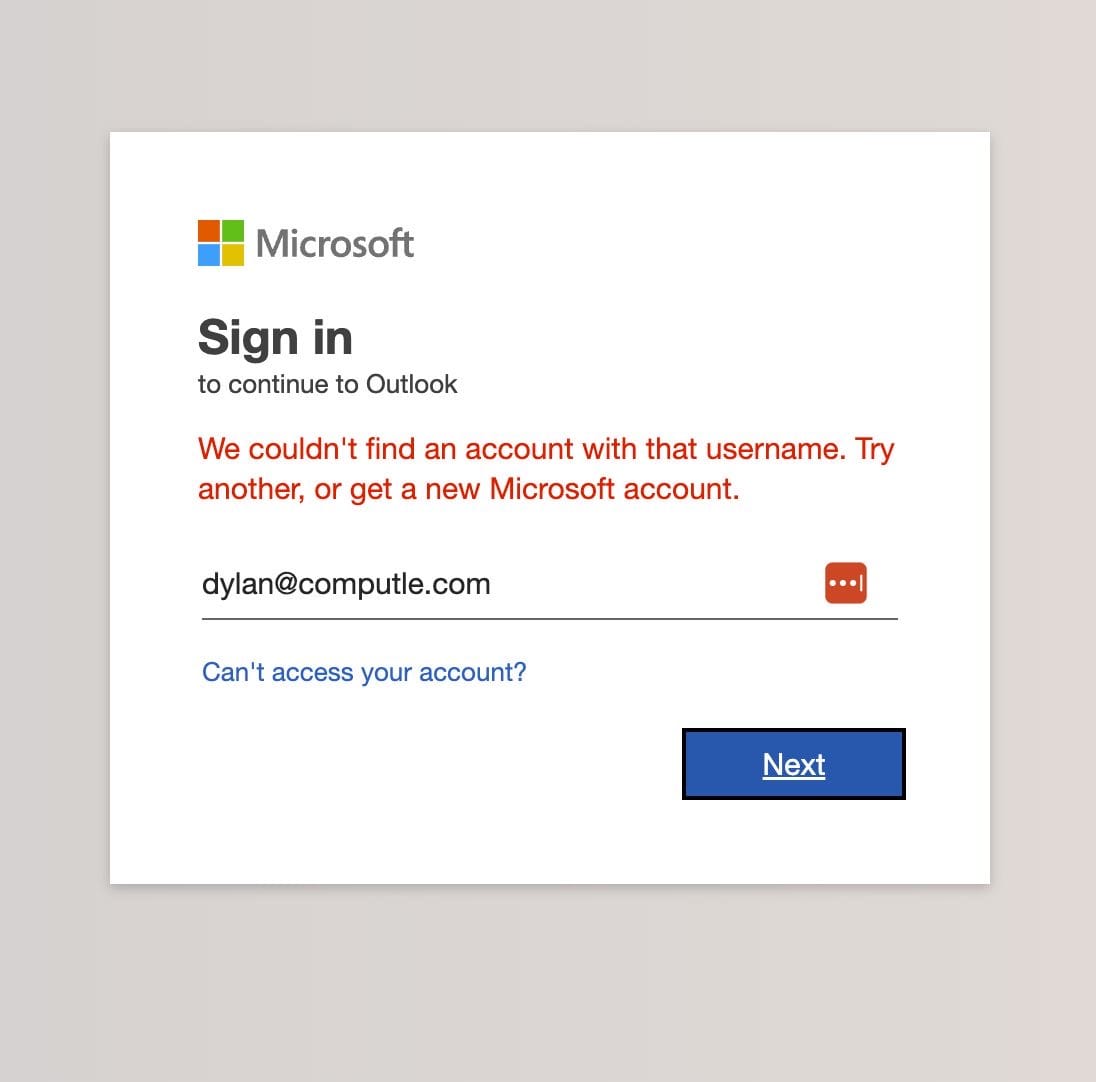
Yesterday, I received an email from HR (me) informing me (the owner) that I was getting a pay rise. Intrigued to see this attack in real life, I played along. This is what I saw.
It started with an email from a Japanese domain
What surprised me the most was the level of sophistication in this first email. They had scraped our webclip icon (albeit with poor compression) and you could be forgiven for thinking that it was genuine. Of course, the M365 known sender banner alerts us that this is not from within our tenant, and the domain is definitely not our of ours.
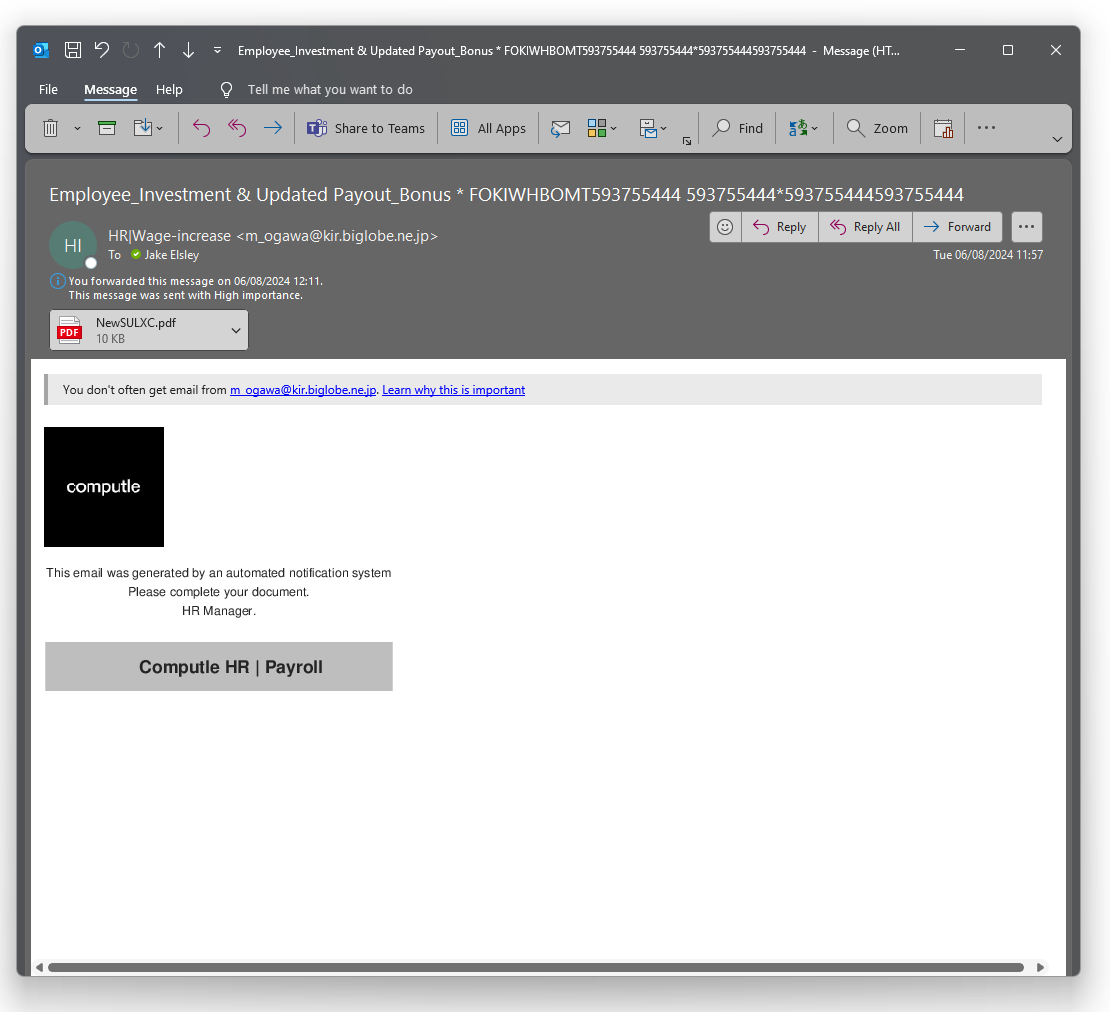
Within the PDF is a QR code
I assume this is to get you to leave a corporate controlled device where security controls may be reduced.
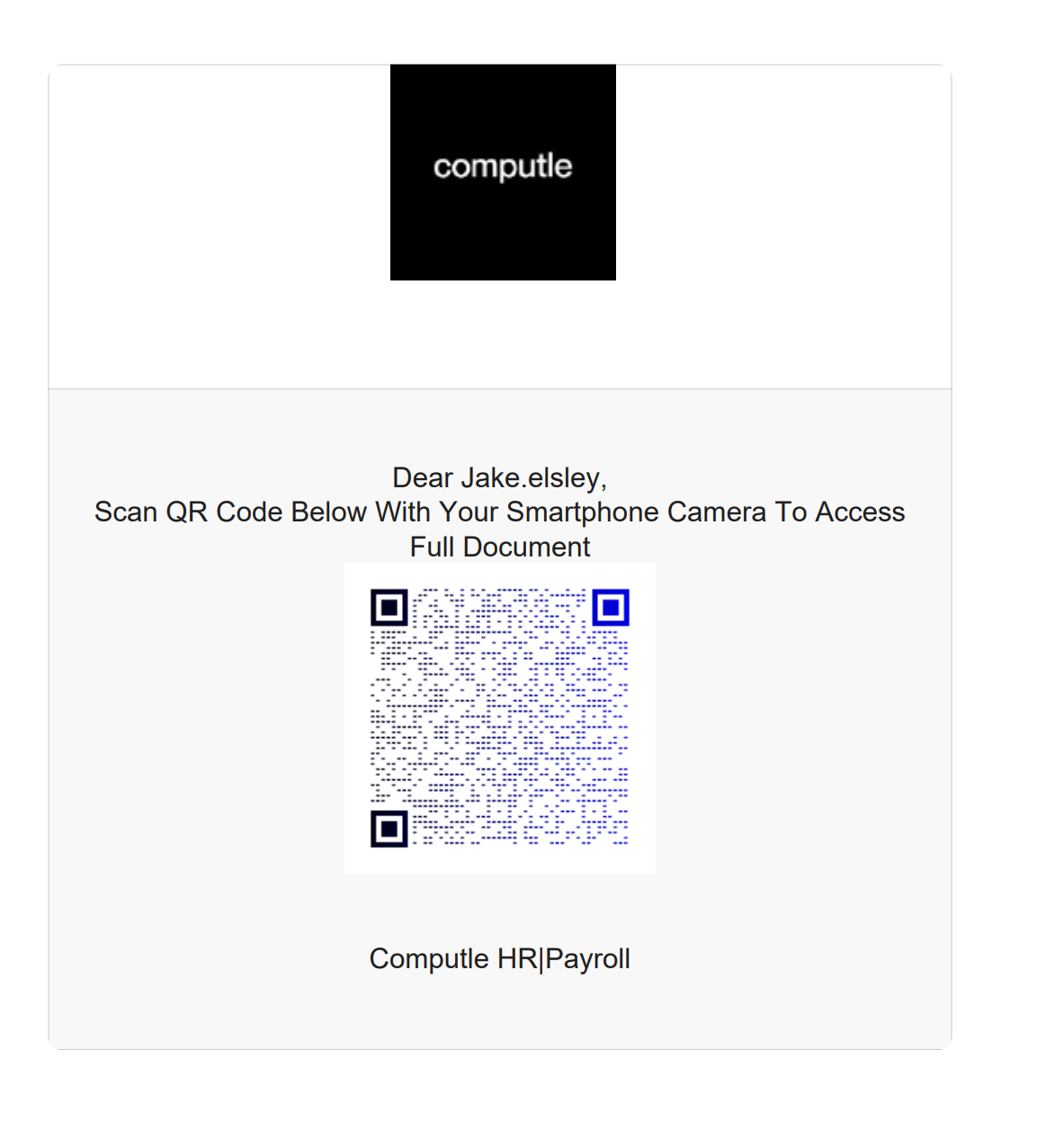
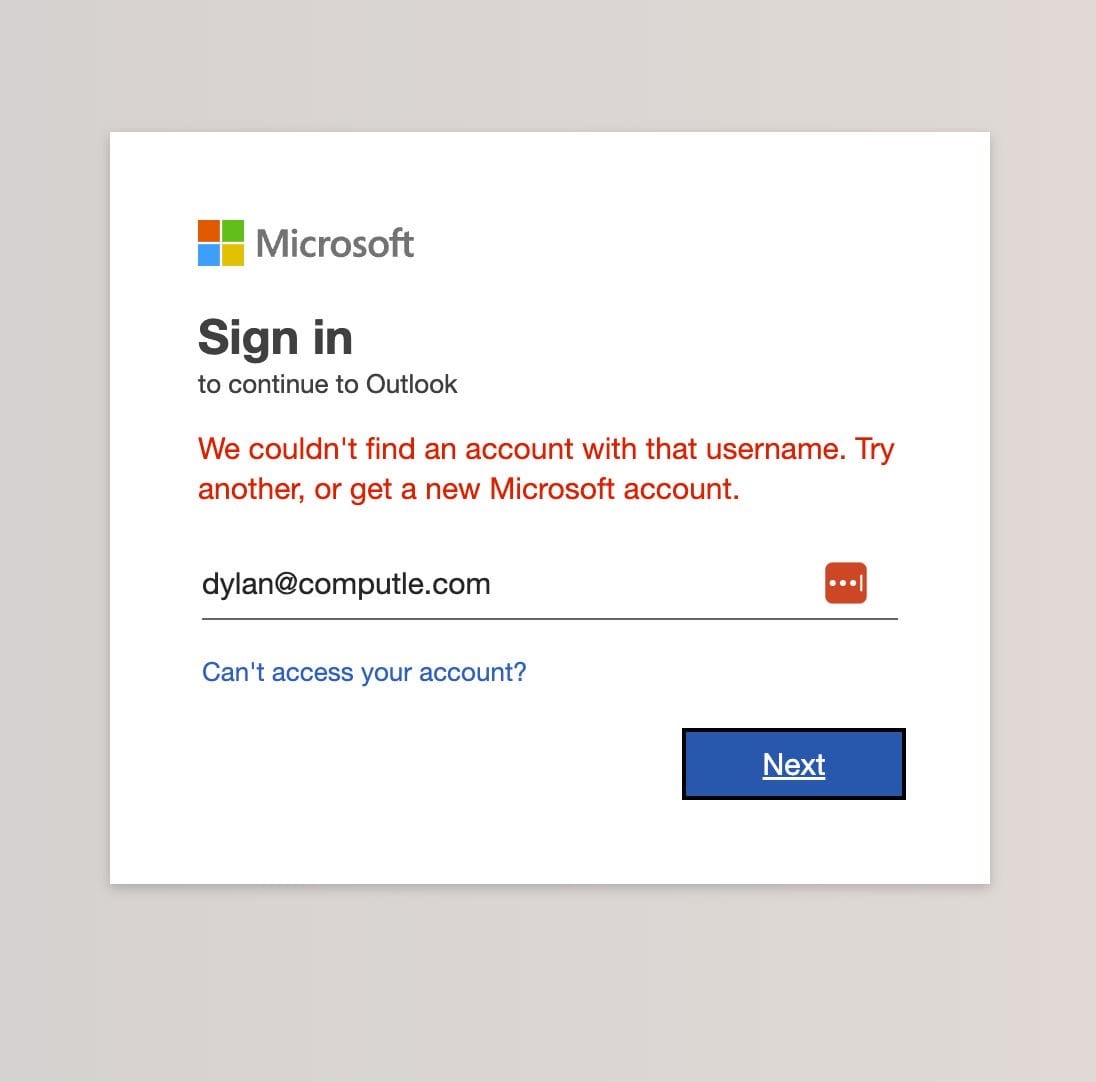
You are then presented with a M365 login page
This is where it gets really interesting. I won't speculate on how they do this, but not only does it capture the login wallpaper from our tenant, but it also provides user validation, showing an error message if the account does not exist in our tenant.
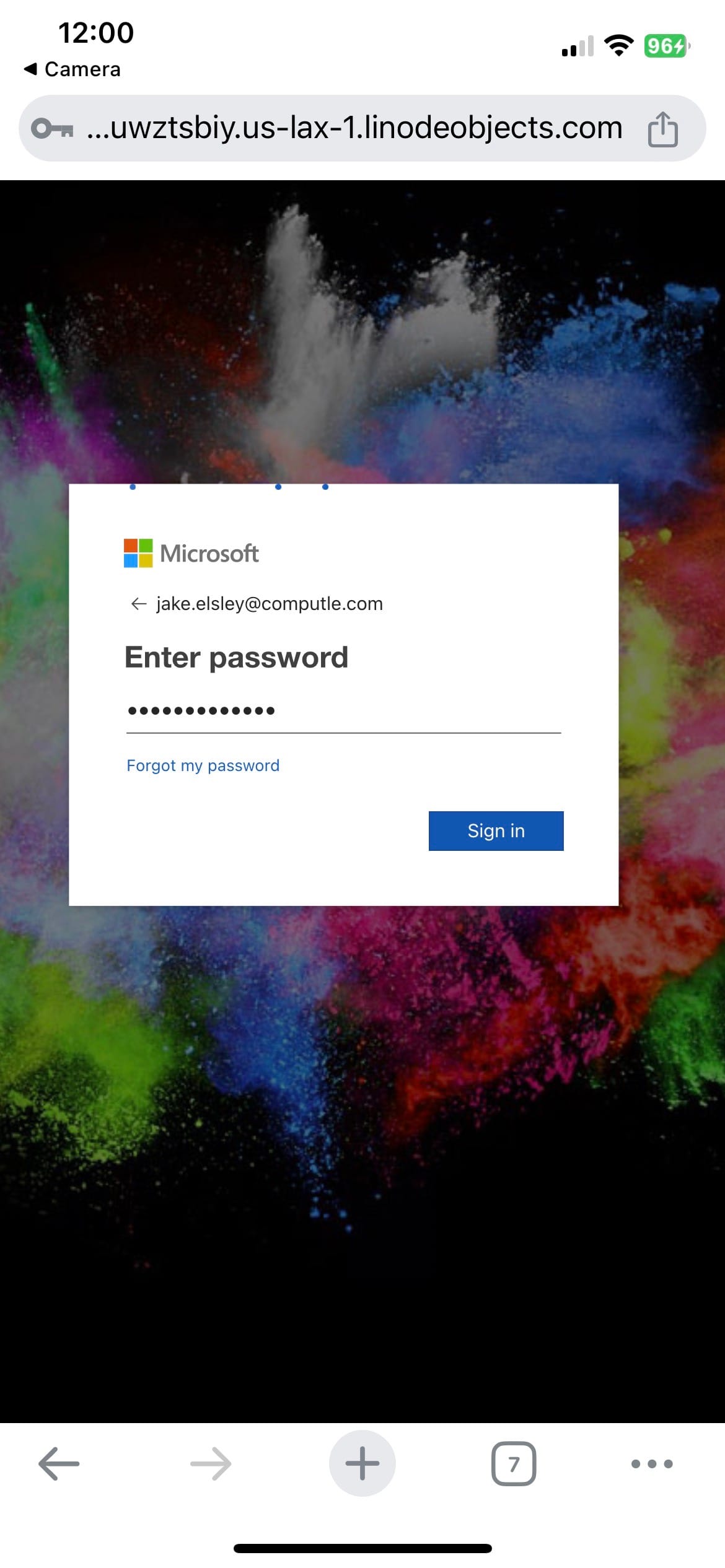
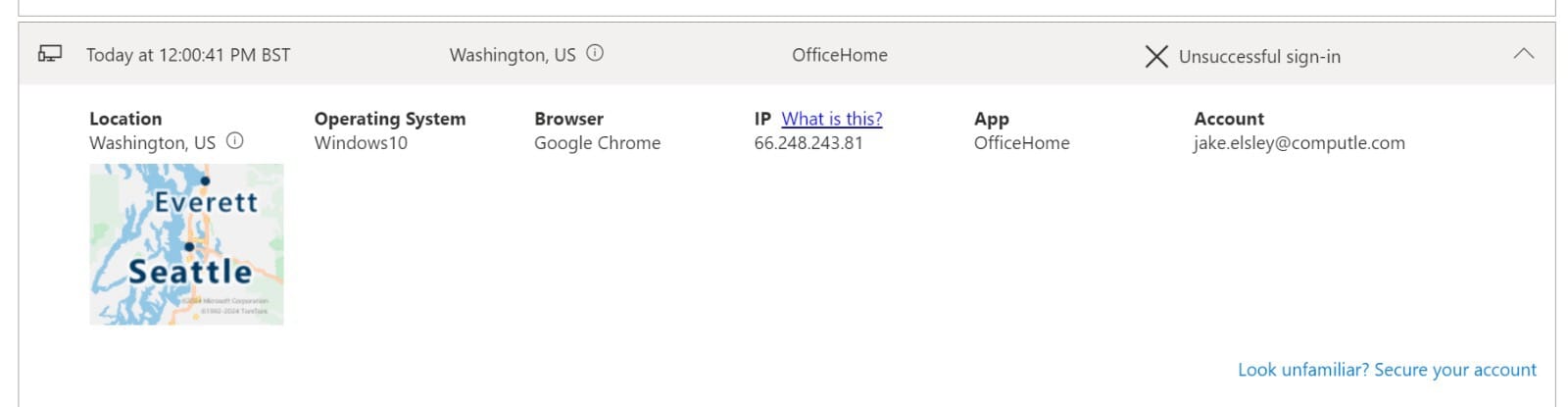
This is then live-tested within your tenant
Of course, I provided a dummy password. But as soon as I did, the login was tested from what could be considered a "known location", Washington US. I have long questioned the efficacy of IP or geo-based restrictions, as it is so easy to spoof your actual location. For the M365 known location flag, this most likely would have been deemed a safe location.
FIDO and Zero Trust to the rescue
Within Computle, we utilise phishing-resistant FIDO2/WebAuthn hardware keys in association with device attestation rules. If a user did enter their genuine password, and this was relayed to the attacker, they would be unable to access the resource from a non-trusted device, and unable to pass the MFA check.
I have reported this domain to Linode, NCSC, Microsoft, and Google Chrome's phishing reporting scheme. At the time of writing, the page is not being flagged as suspicious.
You can blacklist the domain by adding the information below to your firewalls:
piopkeitvcpnvcxapusjhwuwztsbiy.us-lax-1.linodeobjects.com





