Zero Trust and VDI: How to Secure Access with Computle

One drawback in conventional VDI solutions lies in their lack of compatibility with Zero Trust principles, particularly regarding Device Health Attestation on the connecting device.
Device health attestation is a security feature that allows an organisation to ensure that devices attempting to access its resources are healthy and meet its security standards.
Traditionally, this challenge has been addressed through the utilisation of Zero Clients. However, as organisations increasingly adopt Bring Your Own Device (BYOD) policies, organisations can be reluctant to hand out yet another device to end users.
In this article, I'll share how Computle internally utilises modern software-defined security measures to gain insight into device health (antivirus, updates, etc) and how you can do the same, for free.
How Computle Does Zero Trust: Cloudflare
We have been using Cloudflare Zero Trust internally for years and it is a solid and feature-rich platform.
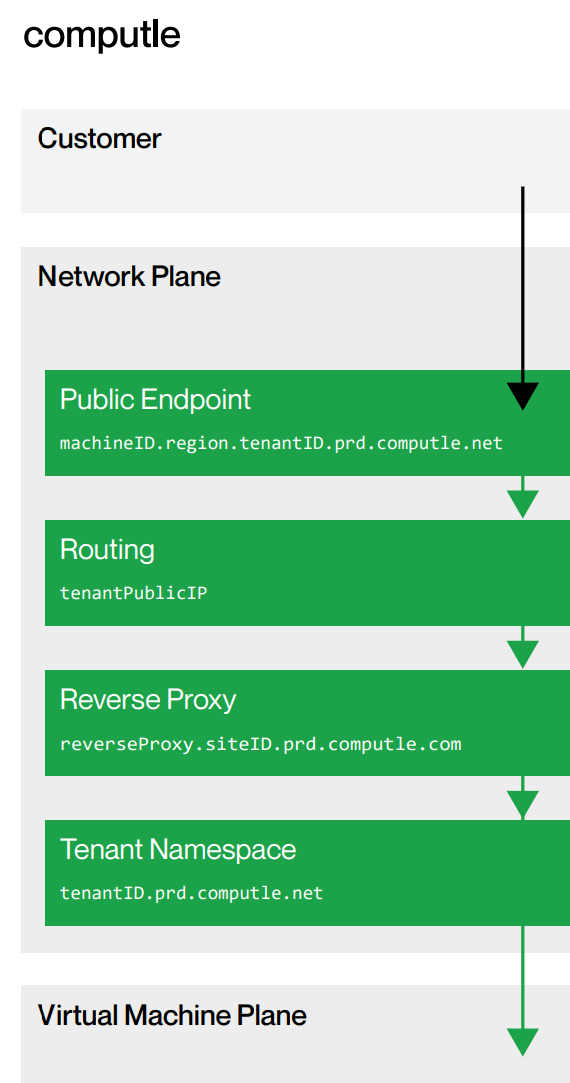
Before I explain how we use it, let's briefly discuss the architecture of Computle:
- Each customer is assigned a tenantID;
- Their users connect to a brokering service which routes them to their assigned machine;
- The user then authenticates using Windows authentication, either via local auth, or more commonly, Active Directory/EntraID.
Whilst this offers a very simple way to access their machines, you are then reliant upon Windows authentication (with optional DUO MFA) as your primary security layer.
Cloudflare Zero Trust establishes an outbound tunnel from your tenant's network which then allows authenticated devices to join the network for as long as your policy allows. Because of this, we are then able to disable the public inbound access forcing any devices to first pass a Device Health Attestation check, and any additional policies that you configure. Only once the devices meetings compliance can it connect to the Computle machine.
Pros
- Cloudflare Zero Trust can be integrated with Active Directory/EntraID
- It is free for up to 50 users.
- The routing is very efficient, with our traffic sent via a nearby Cloudflare data centre.
Cons
- Your traffic is tunnelled/routed via Cloudlflare which does add 10-30ms of latency. Whilst this is fairly unnoticeable within the same region, users in other countries may experience better performance connecting directly.
- Service outages, whilst rare, do happen. However, Cloudflare are very fast to respond and their post mortems are I think the most transparent on the internet.
Our MFA Layer: Duo
To ensure that both the device and the connecting party are authentic, we also integrate Cloudflare with Duo and utilise physical hardware tokens for our MFA. Whilst this step is not strictrly required for Zero Trust, it can offer a frictionless way to add secondary authentication.
There are two ways to integrate Duo into Cloudflare and Computle:
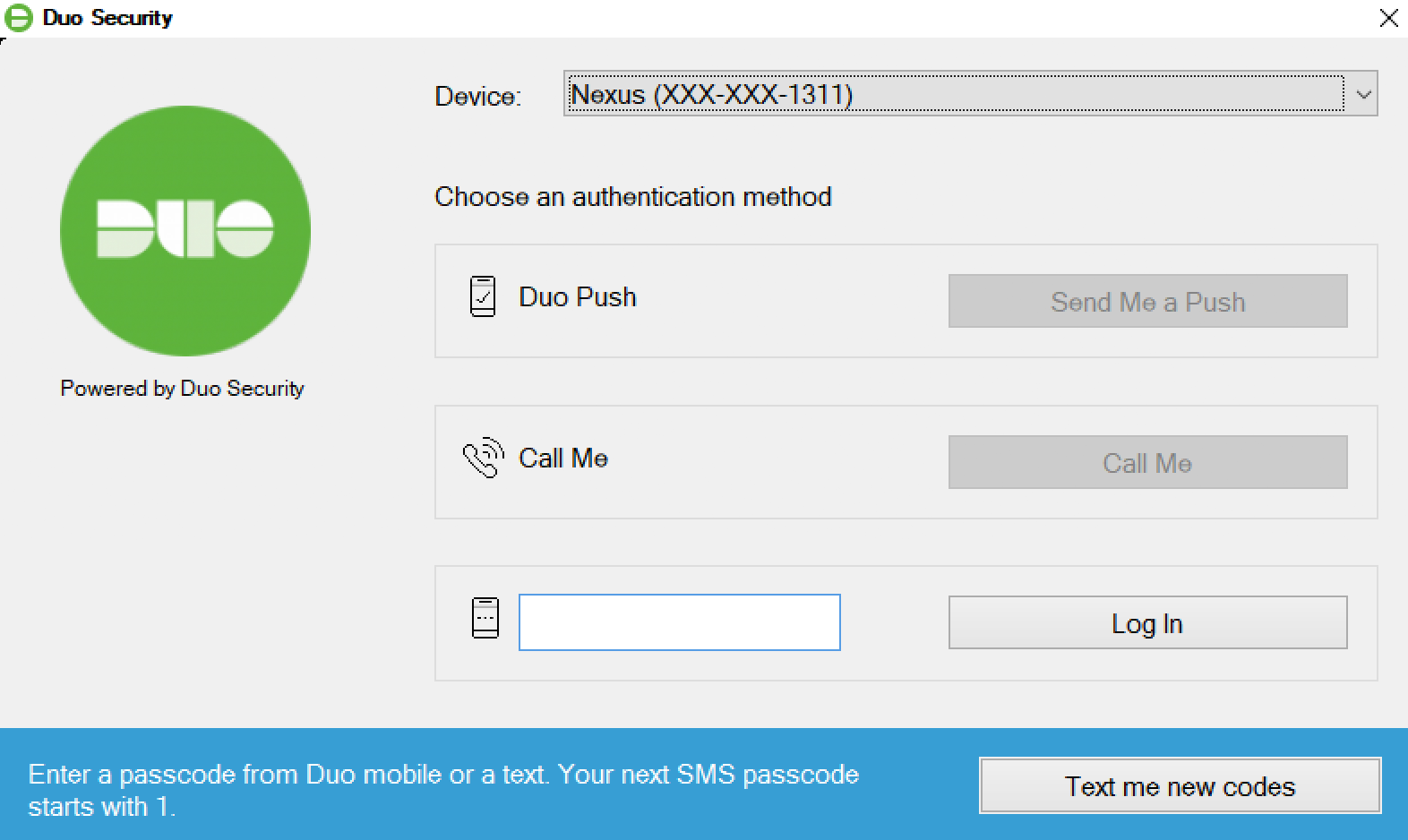
- Install Duo for RDP (easiest): This is probably the easiest way to add MFA to Windows. When connecting, users will see this prompt on their mobile. Alternatively, you can use hardware tokens.
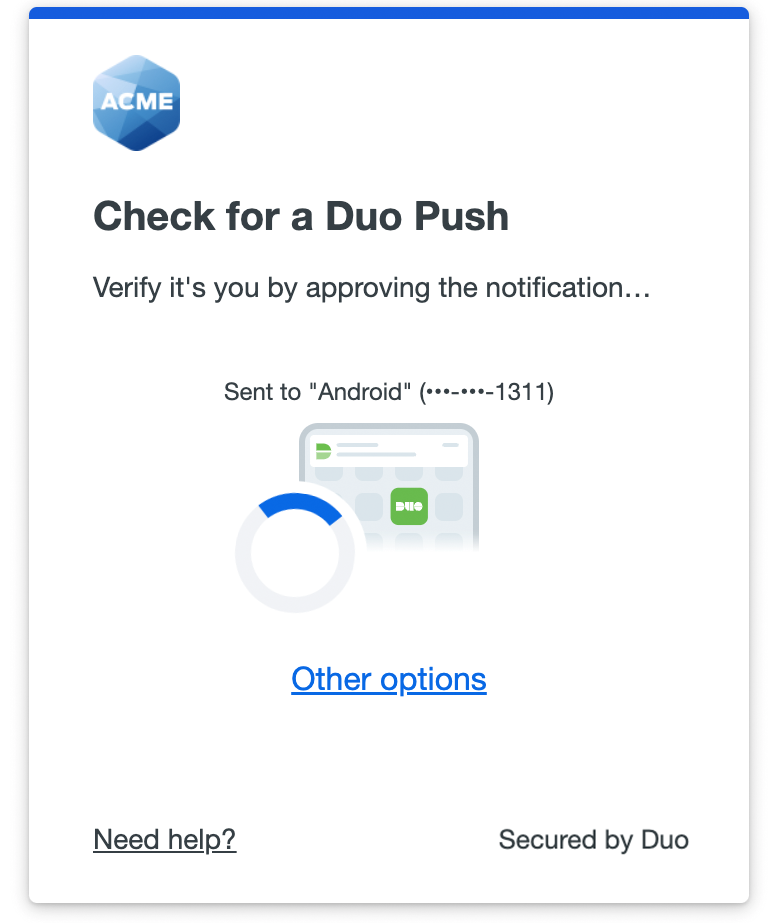
- Use Duo to authenticate a Cloudflare session (less friction): One preferred route is to have Cloudflare Zero Trust authenticate that the device is healthy, and then require the user to verify their identity (via MFA) on periodic intervals. The added benefit here is the more simper end user experience, with Cloudflare only prompting if their location changes, or they show unusual behaviour. With Duo for RDP, there is limited understanding of where the user is connecting from, so the default behaviour is to prompt on every connection.
Honorary Mention:
Whilst Cloudflare are in our eyes the market leader for Zero Trust, two other platform competitors have since released similar offerings. They are:
- Duo Network Gateway, and;
- Microsoft Entra Private Access (Preview).
Duo Network Gateway has the benefit of being installed within Computle, thus reducing any additional latency. Think of this like a traditional site-to-site VPN product. For us, the setup is more complex than Cloudflare, but if you require more advanced features, Duo Network Gateway may be for you.
Microsoft Entra Private Access (Preview) is certainly a more complex beast than either of the other two platforms, but existing users of the Microsoft Enterprise suite (E5, and possibly E3) benefit from inclusive access to this tool. Whilst that may change when the product enters General Availability, users with strength within Intune Device Compliance may prefer an all-Microsoft solution. Our testing of the product has been positive, however, at the time of writing, the endpoint routing locations are limited, meaning traffic latency was higher than Cloudflare.
Join leading animation and AEC firms and discover how Computle's workstation subscription can boost your firm's productivity.





